Setting up Local Administrator Password Solution (LAPS)
LAPS provides a solution to the issue of using a common local administrator account with an identical password on every computer in an active directory domain. LAPS resolves this issue by setting a different, random password for the common local administrator account on every computer in the domain. The local administrator password is stored in Active Directory (AD) as a attribute of the computer and is protected by an Access Control List (ACL) of who can view/modify the attribute.
LAPS can be downloaded as an MSI from http://aka.ms/laps. It is supported on Windows Vista and greater, the solution requires an agent (AdmPwd GPO Extension) installed on client computers to modify the admin password. The MSI also includes an option to install the management tools including a fat client UI, PowerShell module and GPO editor templates.
At the time of writing the current version of LAPS is 6.2
Installation
Installation is done in 3 parts
- Install LAPS agent on client computers
- Upgrade AD schema
- Copy ADMX templates into the SYSVOL
Deploy LAPS Agent
LAPS agent can be installed from any number of software deployment solutions including Active Directory Group Policy, Microsoft System Center, PDQ Deploy or manually run on the agent on the client computer.
Silent install LAPS x64 agent from command-line.
msiexec.exe /i "LAPS.x64.msi" ALLUSERS=1 /qn /norestart
Silent install LAPS x86 agent from command-line.
msiexec.exe /i "LAPS.x86.msi" ALLUSERS=1 /qn /norestart
Update AD Schema
To update the AD schema you will need the following items:
- Be a member of the “Schema Admins” security group
- LAPS PowerShell Module (Can be obtained from the MSI)
- PowerShell Console with Remote Server Administration Toolkit (RSAT)
Once you meet the above criteria you can run Update-AdmPwdADSchema to perform the schema upgrade. The command should show output with a status of “Success”. If all status returns “Success” then you can move on to configuration, if you get an error message or and status returns “Failure” you will need to troubleshoot the problem.
Copy ADMX Templates into SYSVOL
In the following examples ‘contoso.com’ is the active directory domain.
- Copy AdmPwd.admx from C:\Windows\PolicyDefinitions into \\contoso.com\SYSVOL\contoso.com\Policies\PolicyDefinitions
- Copy AdmPwd.adml from C:\Windows\PolicyDefinitions\en-us into \\contoso.com\SYSVOL\contoso.com\Policies\PolicyDefinitions\en-us.
Configuration
Configuration is done in 2 parts
- Configure AD Permissions
- Configure Group Policy
Configuring AD Permissions
In the following examples ‘Contoso Computers’ is the OU in which client computers are located and ‘LAPSAdmins’ is the security group used to grant view/reset ACL permissions of Local Passwords..
The first step in the configuration is to set the permission for which computers can update their own AD account with the new ms-Mcs-AdmPwd and ms-Mcs-AdmPwdExpirationTime attributes added during the schema update. The OU you specify in the following command will grant the OU specified and any sub-OU SELF permission for the 2 attributes.
Set-AdmPwdComputerSelfPermission –Identity "Contoso Computers"
The second step in the configuration is to grant a security group access to view/reset local passwords, This is performed by running the following 2 commands.
Set-AdmPwdReadPasswordPermission –Identity "Contoso Computers" –AllowedPrincipals "contoso.com\LAPSAdmins"
Set-AdmPwdResetPasswordPermission –Identity "Contoso Computers" –AllowedPrincipals "contoso.com\LAPSAdmins"
Configuring LAPS GPO
Do NOT apply the GPO to the ‘Domain Controllers’ OU or install the software or your Domain Controllers.
Create a new GPO and go to Computer Configuration/Policies/Administrator Templates/LAPS. There are 4 possible policies that can be configured:
- Password Settings
- Name of administrator account to manage
- Do not allow password expiration time longer than required by policy
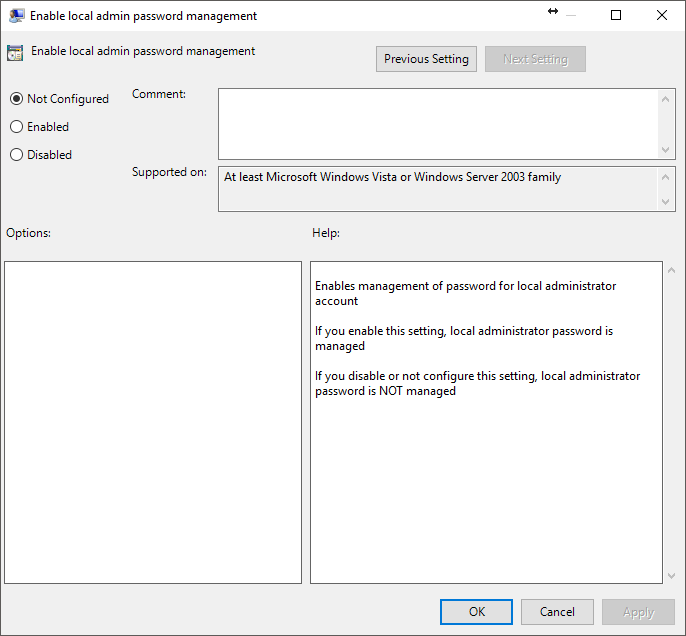
- Enable local admin password management
The only policy that is mandatory to enable to turn on LAPS is Enable local admin password management once this is enabled computers will begin to change their administrator password and store the new password in AD as an attribute of the computer account.
Management
Viewing/Resetting passwords can be done via GUI or CLI.
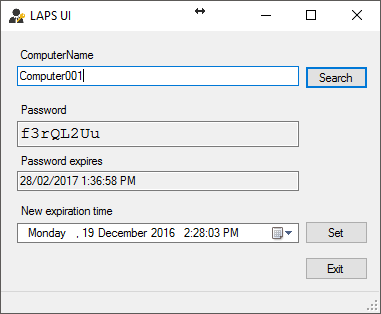
Viewing/Resetting passwords with Fat Client UI
This is self explanatory you can type a name of the computer search which will show the results in the window and allow you to modify the expiration time if you have access.
Viewing/Resetting passwords with PowerShell
In the following examples Computer001 is the computer name used but this can be any computer name in your AD or an array of computer names.
Viewing a password using the LAPS PowerShell module.
Get-AdmPwdPassword –Computername "Computer001"
Viewing a password using the AD PowerShell module.
Get-ADComputer –Identity "Computer001" -prop ms-Mcs-AdmPwd,ms-Mcs-AdmPwdExpirationTime | Select-Object @{Name="ComputerName";Expression={$_.Name}},DistinguishedName,@{Name="Password";Expression={$_."ms-Mcs-AdmPwd"}},@{Name="ExpirationTimestamp";Expression={(Get-Date 1/1/1601).AddDays(($_."ms-Mcs-AdmPwdExpirationTime")/864000000000)}}
Reset a password using the LAPS PowerShell module.
Reset-AdmPwdPassword –Computer "Computer001" –WhenEffective (Get-Date).AddDays(-1)
Reset a password using the AD PowerShell module.
Set-ADComputer –Identity "Computer001" –Replace @{"ms-Mcs-AdmPwdExpirationTime"=0}